In a rapidly evolving digital environment, cybersecurity businesses-especially those with limited marketing budgets-must find innovative ways to stand out. Whitepaper marketing offers a powerful strategy for delivering authoritative insights, establishing thought leadership, and enhancing the content marketing strategy via SEO. Below is a comprehensive guide that explains how to create, distribute, and capitalize on whitepapers in a competitive cybersecurity landscape.
Why White paper Marketing Matters for Small Cybersecurity Businesses
Let’s talk about why whitepaper marketing is such a game-changer for small cybersecurity businesses. In a world where it feels like the big players have all the advantages-massive budgets, endless PR campaigns-whitepapers give smaller businesses a real shot at standing out, building trust, and creating engagement that actually matters. Here’s why this strategy works so well.
Why Cybersecurity Needs Reliable Information
The cybersecurity market is exploding, with projections showing it’ll hit $287 billion in 2027. With that kind of growth, there’s a huge appetite for reliable information and actionable solutions. But here’s the challenge: small businesses are up against competitors with deep pockets. The solution? Focus on cost-effective Strategies that make an impact-like whitepapers-that help you carve out your space in this crowded market are crucial for any marketer.
How Whitepapers Build Trust and Authority
Here’s the thing: trust is everything in cybersecurity, especially when it comes to using white papers as a marketing tool. People aren’t just buying a product-they’re buying peace of mind. Great White paper help you show that you really know your stuff. By sharing in-depth report, data analysis, and insights on real-world challenges, you’re not just promoting your business but positioning yourself as a thought leader. And decision-makers are drawn to companies that demonstrate real expertise, whether it’s breaking down threat intelligence or simplifying compliance.
Purpose of a White Paper to Marketer
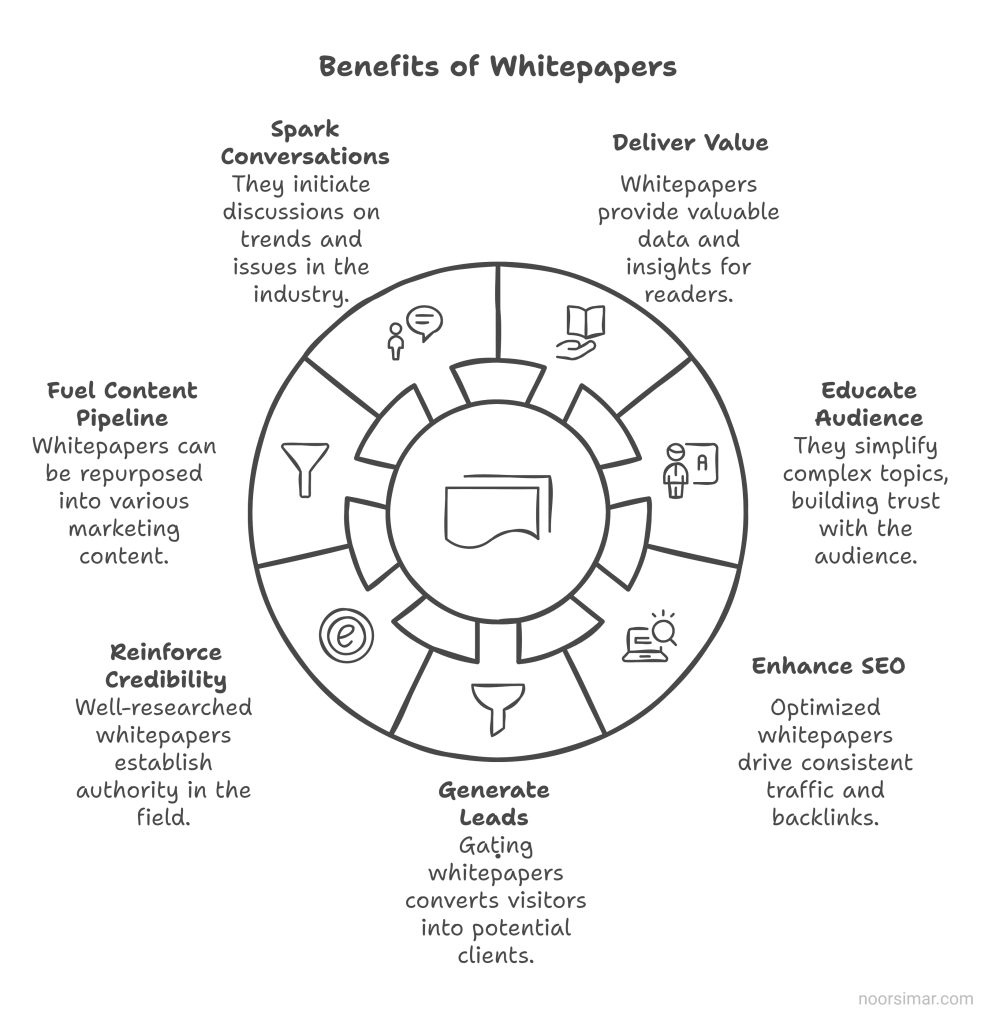
- They Deliver Real Value
Whitepapers are packed with useful information-data, research, step-by-step guides. It’s the kind of stuff people bookmark and actually refer back to. - They Educate Your Audience
Cybersecurity is complicated, right? Whitepapers help simplify it, explaining common threats and best practices in a way that builds trust. - They Work for SEO
A good whitepaper isn’t just a one-and-done deal. When optimized, it can bring in consistent traffic and backlinks over time, becoming an evergreen asset for your business. - They Generate Leads
Gating your whitepaper behind a sign-up form can turn casual website visitors into warm leads. Each download represents a potential client interested in your specific offerings. - They Reinforce Brand Credibility
Publishing a meticulously researched whitepaper positions you as an authority-both in the eyes of potential clients and industry peers. It’s proof you’ve done your homework. - They Fuel Your Content Pipeline
You can repurpose sections of your whitepaper into blog posts, social media snippets, and email campaigns, keeping your marketing channels fresh without reinventing the wheel. - They Spark Meaningful Conversations
Whitepapers often tackle hot-button issues or emerging trends. Sharing your stance can initiate deeper discussions with prospects, partners, and influencers in the cybersecurity community.
Digital White papers are the perfect mix of authority, education, and SEO firepower-all wrapped up in one. Ready to see how they fit into a broader B2B strategy? Let’s dive in.
Understanding Whitepapers: The Secret to Effective B2B Marketing
What Is a Whitepaper in Marketing?
A whitepaper is a long-form, data-centric publication aimed at exploring specific problems and presenting evidence-backed solutions.
In cybersecurity, whitepapers typically cover areas like encryption, threat detection, or regulatory compliance. They serve as educational tools that highlight the complexity of cyber challenges and potential pathways to resolution. For a b2b cybersecurity companies its part of content marketing strategy where the real goal of whitepaper is to get leads though information.
Differentiating Content Formats vs Whitepapers
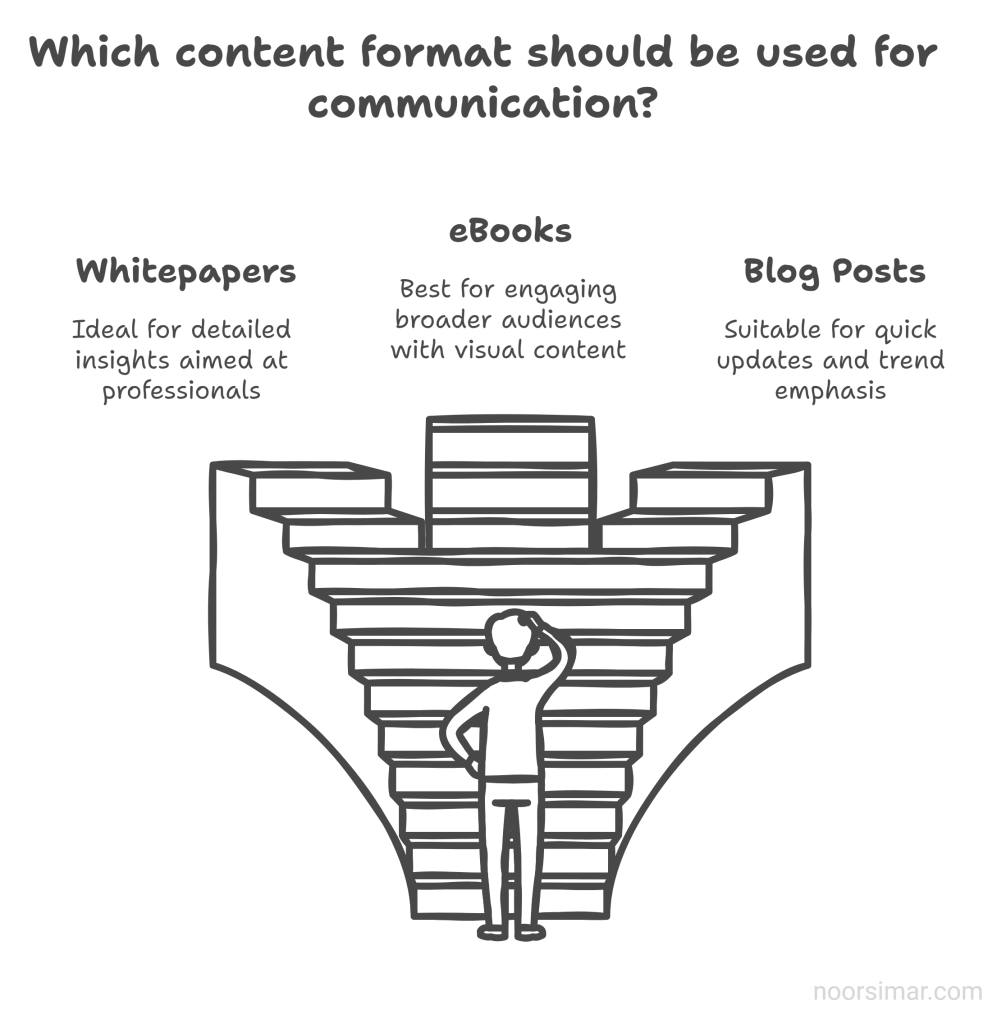
- Whitepapers: Data-heavy, solutions-focused, and aimed at professionals who require detailed insights with long-form content.
- eBooks: More visual and less formal, targeting broader audiences.
- Blog Posts: Shorter, bite-sized content for quick reading; often emphasize trends or immediate updates.
Why Whitepapers Excel in Cybersecurity
Cybersecurity involves intricate jargon and multifaceted compliance requirements; a whitepaper organizes these complexities into structured, understandable segments.
A DemandGen Report reveals that 71% of B2B buyers consider whitepapers to be highly influential when deciding on a product or service as whitepapers have thoroughly cited data (e.g., references to NIST, Forrester, or Gartner) can bolster trust and brand authority, especially in cybersecurity circles.
Psychological Appeal of “Deeper Insights”
It creates an authority bias, and readers are more inclined to trust content that cites industry-leading data and shows expertise, particularly in white papers. With Commitment & Consistency A steady release of high-quality whitepapers signals reliability, enhancing reputational stability.
Having established why whitepapers resonate so strongly, let’s look at how cybersecurity marketing plans can integrate these assets for maximum impact.
How Could a Marketing Plan Relate to Cybersecurity?
Integrating Cybersecurity Into a Broader Marketing Strategy
Integrating cybersecurity into a broader marketing strategy involves aligning secure practices with every marketing channel to reinforce the brand’s identity and promise. By consistently showcasing a commitment to data privacy, compliance, and preparedness, businesses establish trust and position themselves as proactive and reliable, differentiating their brand as one that genuinely “walks the talk” in security.
Defining Core Messaging Around Security white paper
Crafting a whitepaper (or any content) all starts with understanding your ideal customer profile (ICP). Once you’ve nailed that down, aligning your content with their pain points and emotional drivers is key. For example, think about the challenges your audience might face-data breaches, downtime costs, or even the lack of in-house security expertise, which can be a huge issue for smaller or mid-sized businesses.
And then there’s the emotional side. People want simplicity. They’re busy and don’t have time to wade through complicated solutions-they’re looking for straightforward steps to mitigate risks. And don’t underestimate the power of impact. Showing how your solution actively prevents attacks or strengthens compliance can be a game-changer for decision-makers who need measurable results to justify their choices.
Of course, your ICP might look completely different from what I’ve described in the context of B2B content marketing. That’s the beauty of tailoring your approach. If you’re still in the process of building your ICP, you can directly go to Build your ICP section.
Linking Digital Marketing KPIs with Cybersecurity Goals
Let me tell you something I’ve noticed about the smartest CMOs-they don’t get caught up in vanity metrics like “brand awareness” for its own sake. Sure, having more people see your content is great, but the real win? Converting those views into paying customers. That’s where linking your digital marketing KPIs to your cybersecurity goals becomes a game-changer.
Think about it: secure brand representation isn’t just about looking trustworthy-it actively builds audience engagement and recall. And when it comes to lead generation, whitepapers are pure gold. They’re the kind of high-value digital content you can gate behind a lead capture form, meaning every download isn’t just a number-it’s a potential customer. Now, that’s the kind of brand awareness that actually drives results.
And don’t forget to align all your marketing channels with your security goals. Your website? Make sure it’s locked down with SSL certification, trust seals, and a crystal-clear privacy policy to show visitors you mean business. On social media, share cybersecurity tips, real-time threat intel, or compliance updates to foster a knowledgeable, engaged community. Even your email campaigns should reflect your security values by using encrypted links and secure communication. Whether it’s blogging, video marketing, or even starting a podcast, tie it all back to your core mission of building trust and driving action.
Having explored the importance of integrating cybersecurity themes within your marketing efforts, let’s delve into how whitepapers can drive SEO advantages and enhance your brand’s discoverability.
Leveraging Whitepapers for SEO in the Cybersecurity Space
SEO Strategy Overview
- Keyword Targeting: Focus on niche, long-tail phrases like “white paper digital marketing,” “cybersecurity solutions for small businesses,” or “compliance best practices” to attract high-intent traffic with less competition helping you reach the right audience through effective content marketing.
- On-Page SEO: Optimize titles, meta descriptions, headings, and image alt tags with cybersecurity-related keywords. Ensure content includes semantically related terms to improve relevance for search algorithms.
- Content Clusters: Create a network of related blog posts or articles surrounding your whitepaper topic, all interlinked to boost contextual relevance and domain authority.
Boosting Cybersecurity SEO with Whitepapers
- Internal Linking: Link to the whitepaper from high-performing blog posts, service pages, or FAQs to funnel traffic and reduce bounce rates. Use descriptive anchor text for added SEO value.
- External Linking & Citations: Credibility is key in B2B content marketing, especially when your white papers cite authoritative sources. Cite authoritative sources like NIST, Forrester, or Gartner within the whitepaper to enhance it. These citations not only bolster trust but can also encourage backlinks when referenced by other sites.
- Schema Markup: Use structured data (e.g., FAQ schema or report schema) to improve how your whitepaper appears in search engine results, potentially boosting click-through rates.
- Press Releases: Announce the launch of your whitepaper via press release distribution services like PRWeb, Business Wire, or EIN Presswire. Highlight the value proposition of your whitepaper to gain media coverage and authoritative backlinks.
Guest Posting and Syndication
- Guest Posting: Partner with cybersecurity blogs, forums, and industry news sites to publish articles that summarize or expand on your whitepaper. Include backlinks to the full version hosted on your website.
- Syndication: Distribute your whitepaper on platforms like Medium, SlideShare, and LinkedIn Articles to reach broader audiences while pointing readers back to your main site for the full content.
- Localized Syndication: Target industry-specific regional platforms or communities (e.g., cybersecurity forums in APAC or EU markets) to attract a geographically diverse audience.
Securing Long-Term SEO Impact
- Evergreen Content: Periodically update your whitepaper with fresh data, new case studies, or evolving cybersecurity trends to keep it relevant and SEO-friendly.
- Multimedia Content: Enhance engagement by incorporating interactive visuals like clickable charts, animated graphs, or embedded videos that explain complex cybersecurity concepts.
- Repurpose as Microcontent: Break your whitepaper into smaller pieces-infographics, short videos, or social media snippets-and link them back to the full version for maximum exposure.
- Lead Magnets: Use the whitepaper as a downloadable resource gated behind a lead capture form. This not only boosts SEO (by increasing dwell time and engagement) but also fuels your email marketing efforts.
Leveraging User Engagement for SEO
- User Signals: Optimize the whitepaper landing page for longer session durations by including interactive content, summaries, or video walkthroughs, which can improve SEO rankings.
- Encourage Sharing: Add easy-to-use social sharing buttons on your whitepaper’s landing page to increase reach and amplify backlinks from social signals.
- Community Discussions: Share excerpts or insights from your whitepaper in cybersecurity forums like Reddit’s r/cybersecurity or LinkedIn groups, prompting engagement and discussions that link back to your site.
- Webinars and Live Q&A Sessions: Host a webinar or live event where you discuss the whitepaper’s key findings. Use these events to drive traffic and link attendees back to your whitepaper.
Advanced SEO Tactics for Whitepapers
- Competitor Analysis: Analyze top-ranking cybersecurity whitepapers for their keyword usage, backlink sources, and content length to identify areas where you can outperform them.
- Google Discover Optimization: Optimize whitepaper summaries for mobile and use engaging visuals to increase chances of being featured on Google Discover.
- Podcast Mentions: Collaborate with cybersecurity podcasts to discuss key insights from your whitepaper and link back to the document in show notes for additional referral traffic.
- Social Media Retargeting: Use retargeting ads on platforms like Facebook and LinkedIn to bring back visitors who interacted with your content but didn’t download the whitepaper.
Now that the strategic value of whitepapers for cybersecurity SEO is clear, it’s time to break down how to create one that truly resonates-and converts.
Actionable Steps to Write a White Paper that is High-Converting
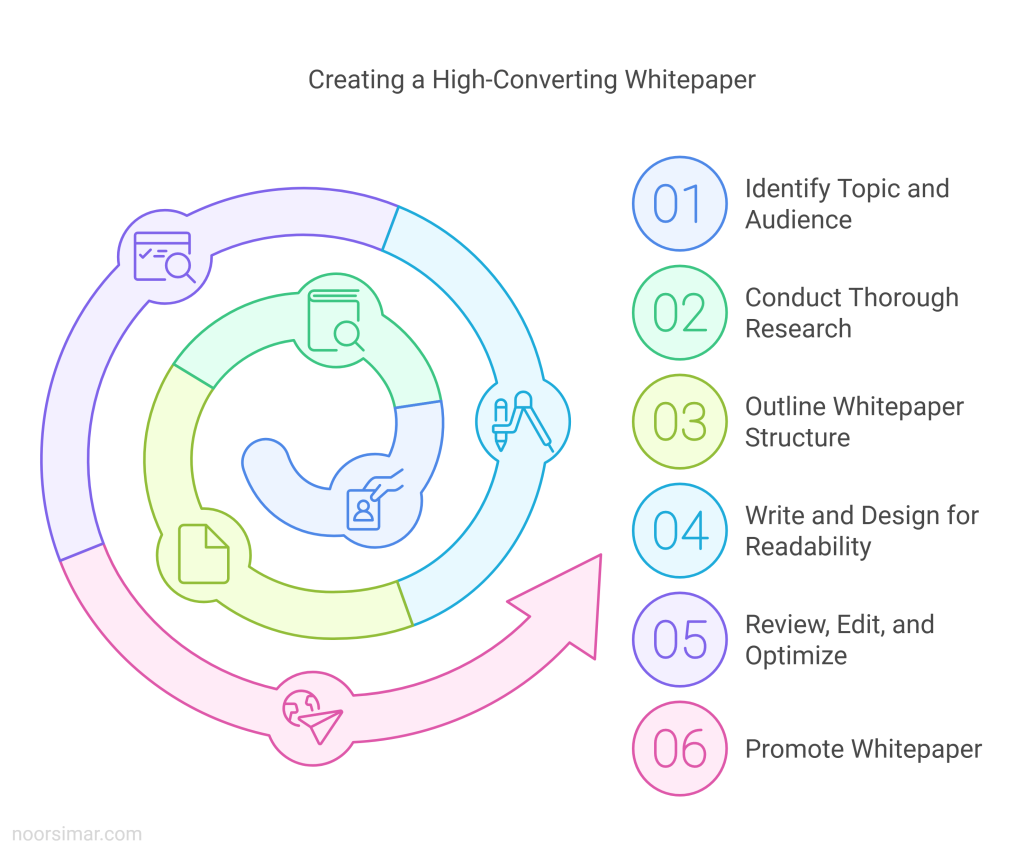
Step 1 – Identify Your Topic and Target Audience
- Pinpoint Key Problems: Conduct research on prevalent cybersecurity issues-such as ransomware or cloud vulnerabilities– for different types of white papers that can resonate with potential clients.
- Assess Audience Needs: Determine if the target demographic wants deeper technical knowledge or a simplified overview of security essentials.
Build Your ICP or Persona Using ICP Builder
- Persona Development: Utilize the ICP (Ideal Customer Profile) builder at https://mokshious.com/persona-builder/ to capture demographics, pain points, motivations, and objections.
- Refine Topic Relevance: You ensure maximum relevance by aligning your whitepaper topic with the specific fears and goals discovered through persona-building.
- Tailor Content Depth: If the ICP suggests decision-makers prefer “big-picture” security over technical deep dives, focus on summarizing critical issues rather than delving into every granular detail.
Effective Brainstorming Techniques
- Competitive Gap Analysis: Investigate competitor whitepapers or blog posts to find unaddressed topics or subtopics.
- Social Listening: Monitor platforms like Quora, Reddit, and specialized forums to uncover recurring questions or concerns.
- Sales & Support Team Insights: Gather feedback on the issues customers repeatedly raise.
With a clear sense of who you’re speaking to and which topics will captivate them, the next step is to gather robust, credible data that substantiates your claims.
Step 2 – Conduct Thorough Research
- Comprehensive Fact-Finding: Gather stats from reputable bodies like Verizon’s Data Breach Investigations Report, Cisco Security studies, or government cybersecurity agencies.
- Expert Interviews: Consult with internal security analysts or external professionals to add authoritative quotes and firsthand perspectives.
Organizing and Evaluating Data
- Focus on Relevancy: Select data that addresses actual pain points and highlights cost or risk implications for small businesses.
- Categorize Findings: While creating white papers make sure to further research findings and Group related data points under clear headings, which will simplify writing and white paper design later.
After collecting the necessary data, the challenge becomes structuring your whitepaper in a way that is logical, compelling, and easy to follow.
Step 3 – Outline Your Whitepaper Structure
- Introduction & Executive Summary: Overarching problem statement, targeted insights, and promised solutions.
- Problem Statement: A deep dive into how security lapses or specific threats can devastate business operations.
- Solution Overview: Detailing potential strategies-such as a cloud-based approach or compliance frameworks-to mitigate risks.
- Case Studies: Provide real-world transformations or success stories.
- Actionable Checklists: Compile step-by-step guidelines that readers can implement immediately.
- Conclusion & Next Steps: Summarize main insights and prompt readers to reach out or explore further resources.
Structuring Template for Maximum Readability
- Heading Hierarchy: Employ H2, H3, and H4 levels to segment complex concepts.
- Visual Aids: Use bullet points, graphs, and images to make lengthy sections more accessible and appealing of your white papers and marketing content.
With a solid framework in place, it’s time to turn that outline into a polished, visually engaging document that resonates with your intended audience.
Step 4 – Write and Design for Readability
- Concise Writing Style: Short paragraphs with transition words help maintain the reader’s attention.
- Data Visualization: Charts, tables, or infographics turn complex numbers into digestible visual elements.
Ensuring Accessibility
- Color Contrast: Adhere to accessible color guidelines for infographics and charts to improve the effectiveness of your white papers.
- Alt Text: Provide descriptions of each graphic, ensuring inclusivity for users relying on screen readers.
Transition to Next Section
Once the whitepaper is drafted and designed, the final touches-proofreading, SEO, and strategic CTAs-can make a world of difference in performance.
Step 5 – Review, Edit, and Optimize
- Professional Editing: A thorough proofreading pass avoids typographical errors that can undermine credibility; it is the purpose of a white paper to present information clearly. Pro Editing also maintains high-quality marketing content that resonates with your persona.
- SEO-Friendly Copy: Integrate your main keywords-such as “whitepaper marketing” or “cybersecurity SEO”-in headings and meta descriptions without overstuffing.
- CTA Placement: Insert calls to action (e.g., contact forms, subscription offers) at logical breakpoints, like the end of major sections.
A/B Testing CTAs
Any whitepaper should also be presented in web page format, as well as in PDF and slide(PPT) formats. There’s more repurposing that can be easily done (as discussed in Step 5) – but Webpage, PDFs, and Slides are must-haves.
- Variation in Wording: Try subtle changes in Copy-“Get Your Security Blueprint” vs. “Download Our Free Whitepaper”-to identify which resonates better.
- Monitor Analytics: Measure conversion rates, click-throughs, and user behavior to refine future whitepapers.
After perfecting your whitepaper, the next phase revolves around strategic promotion-ensuring your work reaches the right audience through dedicated landing pages, email sequences, and more.
Promoting Your Whitepaper: A Step-by-Step Guide
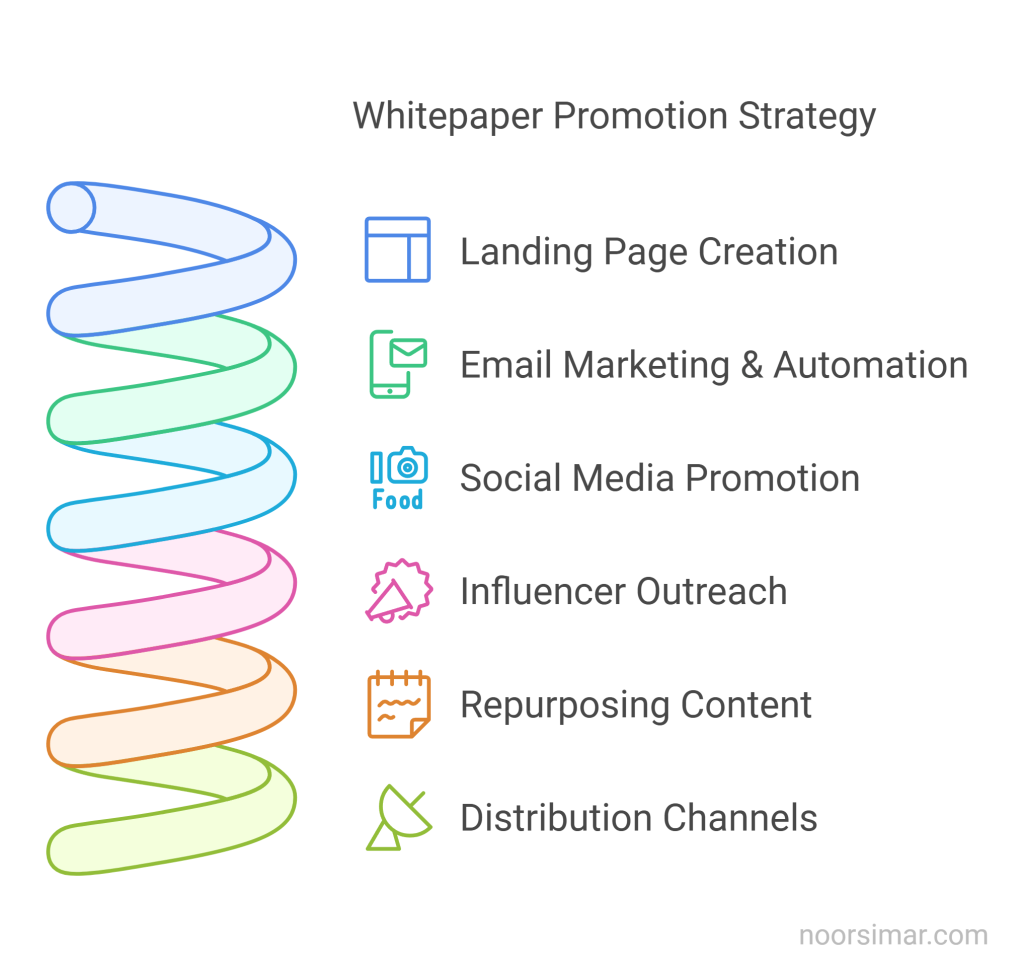
Step 1 – Landing Page Creation
- Dedicated Page: Feature a compelling headline that pinpoints the whitepaper’s value, followed by a concise sign-up form that aligns with your marketing team’s objectives.
- Trust Elements: Include certificates, user testimonials, or short quotes from known industry figures to endorse the whitepaper’s value and have a ripple effect in marketing.
Crafting Persuasive Landing Page Copy
- Urgency & Exclusivity: Mention limited availability or cutting-edge data only found in your whitepaper.
- Mobile Optimization: Ensure that mobile visitors have a seamless experience, as an increasing percentage of B2B traffic comes from smartphones, which is crucial for your ROI.
With a high-converting landing page in place, multi-channel promotion can further amplify your reach, starting with email marketing and segmentation.
Step 2 – Email Marketing & Automation
- Segmentation: Tailor email sequences based on whether recipients are new leads(Cold) existing clients(Warm) or specific individual who have asked for the Whitepaper(Hot) via Marketing Automation.
- Drip Campaigns: Content marketers can strategically reveal portions of the whitepaper content, gradually building anticipation for the final full download.
Personalizing Emails
- Dynamic Merge Fields: Insert the subscriber’s name, company, or past interaction points for deeper relevance.
- Behavioral Triggers: If your cyber business is SaaS related, you must have a lot of Behavioral triggers; if a recipient clicks a particular option, searches for something, or follows up with related resources; Send an invitation to download the whitepaper.
Now lets discuss on how Social channels can boost organic shares and industry credibility-an essential step for whitepaper success in content marketing.
Step 3 – Social Media Promotion
- Platform-Specific Messaging: LinkedIn posts can be more data-heavy; Twitter updates thrive on succinct stats.
- Industry Groups & Communities: Engage in knowledge-sharing discussions on forums and social channels dedicated to cybersecurity.
Effective Hashtag & Community Use
- Hashtag Research: Identify trending, relevant hashtags like #cybersecurity, #dataprotection, #infosec.
- Community Interaction: Avoid spamming. Offer value in group discussions and guide interested users to your whitepaper when relevant.
Beyond social media, leveraging influencers and industry experts can spark conversations and lend added authority to your content.
Step 4 – Influencer Outreach
- Early Access Invitations: Grant cybersecurity experts or influencers a sneak peek, paving the way for genuine endorsements.
- Credibility Boost: Even short quotes from reputable influencers can significantly heighten a whitepaper’s authority and effectiveness as marketing collateral.
7 Sites to Connect with Cybersecurity Influencers
- X Threads
- LinkedIn (Security-focused groups)
- Peerlyst
- Cybersecurity Insiders
- Reddit r/cybersecurity
- BrightTALK
- Spiceworks
Once influencers and key industry figures share your white paper, it will extend your whitepaper’s life span. But when it comes to b2b content marketing then you must repurpose and redistribute it across multiple channels.
Step 5 – Repurposing Content for Lead generation
- Webinars & Podcasts: Take those key findings and turn them into something people can binge on. Whether it’s a webinar or a podcast; Get those insights out there in a way that’s easy to digest and entertaining to boot.
- Blog Series: Break that whitepaper into bite-sized blog posts. Not everyone has the patience for a 50-page informational document, you know? Give them what they want: quick, actionable insights that hit the spot instead of entire white paper.
7 Sites Where It Can Be Repurposed
- Medium
- LinkedIn Articles
- Slideshare
- Quora
- YouTube
- Vimeo
- Podcast Directories
Finally, deploying the whitepaper in a wide array of distribution channels ensures maximum online and offline visibility.
Step 6 – Distribute Your White Paper
- PDF Directories: Platforms like Issuu or Scribd can host your white paper for extended reach, though its a platform for any marketing materials but sure helps in SEO juice.
- Podcast Mentions: If you run or appear on a podcast, direct listeners to the whitepaper for further reading.
- Exit Popups: Prompt website visitors leaving your site with a final opportunity to download the resource.
- Announcement Banners: Create an announcement banner for your website visitors.
- P.S. Link in Emails: Have PostScript in your email template. Many readers skip to the P.S. line. So, it good idea to use it wisely to draw attention to newly published content; like whitepaper. This encourage downloads and engagement.
Some Sites Where Cybersecurity Whitepapers Can Be Submitted
1. SANS Reading Room
SANS Reading Room is a really respected platform for cybersecurity research. They publish white papers that are deep, technical, and a lot of their content comes from folks working through SANS certification projects. That said, companies can also submit papers, but the bar is high—you really need to show off solid technical expertise. There’s no direct submission form, so you’d have to reach out to them by email at [email protected]. Alternatively, if you’re considering a GIAC certification project for one of your team members, that’s another route to get published in their reading room. Either way, it’s a great place to position us as thought leaders. Make sure to check white paper examples in their reading room for effective marketing collateral.
2. EC-Council Cybersecurity Exchange
The EC-Council Cybersecurity Exchange is a well-known platform for whitepapers in cybersecurity, especially for topics like threat intelligence, IoT security, and emerging threats. Submissions are reviewed for quality and relevance, so it’s another place where we’ll need to put our best foot forward. If accepted, it’s a great way to gain visibility in the cybersecurity community. This could be ideal if we want to highlight any cutting-edge work we’re doing. Here’s the link to submit: EC-Council Cybersecurity Exchange Whitepapers.
3. Help Net Security
Help Net Security is another big player for cybersecurity content though they lean more toward practical and research-based content, so we’d have to make sure it’s not just marketing fluff. You can pitch them [email protected] or visit https://www.helpnetsecurity.com/contact/ to get started, but it’s worth mentioning upfront that we’re submitting a technical white paper, not a press release. Honestly, this could be a great platform for us to connect with decision-makers in the industry.
4. The Hacker News
The Hacker News is a bit of a tougher nut to crack—they’re really selective about what they publish. If we have something groundbreaking, like original research or insights on a new threat, this could be a good option. They don’t have a dedicated submission form for whitepapers, but we can reach out via [email protected] and through their contact page to pitch a guest post. They’re also open to sponsored content if we want to go that route, but even then, it has to offer real value to their audience. Definitely a good option if we want to make a splash with something big.
5. eForensics Magazine
eForensics Magazine is an awesome niche platform for digital forensics and incident response topics. They’re very open to company submissions, as long as it’s technical and provides real value— as always no sales pitches allowed. Creators process is straightforward: you send them an abstract or an outline, and if they like it, they guide you through the rest. This could be a great fit if we want to highlight our expertise in forensics or advanced threat detection.
6. arXiv
arXiv is more academic—think of it as the go-to for cutting-edge research papers. Companies can submit, but it has to be scholarly and backed by proper methodology. If we have something deeply technical, like cryptography research or a new approach to network security, this is the place. arXiv submission process Involves creating an account and uploading a properly formatted PDF, usually in LaTeX, to share your marketing white paper. Moderators do a quick check to make sure the paper is legit before it’s published. It’s not for everyone, but it could really boost our credibility in the academic and research space.
7. SSRN
SSRN is similar to arXiv but a bit broader in scope. They’re totally fine with company-authored papers, especially if it’s related to cybersecurity policy, trends, or research. It’s great for showcasing thought leadership, especially if we want to reach an interdisciplinary audience that includes policymakers and academics. The process is pretty simple: we just create an account, upload the paper, and choose the right eJournal category—like ‘Cybersecurity and Data Privacy.’ It doesn’t need to be peer-reviewed when we submit, which is a plus if you want to promote your white paper out there quickly.
8. StationX
StationX is another fantastic platform to consider for publishing our whitepapers. They accept a range of cybersecurity materials—whitepapers, technical reports, and research papers—but they’re serious about quality. Everything goes through a peer-review process by cybersecurity experts to ensure accuracy and relevance. Their site even provides specific formatting and content guidelines, so we’ll need to align with that. The benefits? Global exposure, industry recognition, and opportunities to network with other professionals. If we’re ready to go all in, here’s the link to their submission page: StationX White Papers.
9. SpringerOpen
SpringerOpen is perfect if we want to take a more academic approach. It’s a peer-reviewed journal that focuses on high-quality cybersecurity research and whitepapers. Submissions have to follow detailed formatting and editorial policies, and the papers undergo a rigorous peer-review process, which is great for credibility. One bonus here is that authors can choose open-access publishing, which means our work could reach a global audience for free. If we’ve got something deeply technical or groundbreaking, this could be a great fit. Submission details are here: SpringerOpen Cybersecurity Submission Guidelines.
10. InfoSec Institute
InfoSec Institute is pretty popular with cybersecurity professionals. They post guest articles and whitepapers — as long as it’s co-branded. The key is to make it educational and vendor-neutral, or at least transparent if it’s specific to our solution. It’s super straightforward—just pitch a topic or send in a draft for their editorial team to review. It’s a great way to show off our expertise and reach a wide audience.
11. Cyber Security Hub (CSHub)
Cyber Security Hub (CSHub) is a solid option if we’re targeting enterprise security professionals. They have a huge collection of cybersecurity whitepapers and are open to submissions from experts in the field. They’re looking for papers that focus on practical insights and real-world applications—things like third-party risk management or AI in cybersecurity. It’s curated specifically for enterprise-level readers, so it could help us connect with the right audience. Check out their submission page here: CSHub Whitepapers.
7 B2B Cybersecurity Podcasts for Extended Reach:
- Security Now
- The CyberWire
- Darknet Diaries
- Cyber Security Today
- CISO-Security Vendor Relationship Podcast
- Smashing Security
- Hacking Humans
With this strong promotional plan in place, let’s examine real-world outcomes to see how effective whitepaper marketing can be for cybersecurity brands.
Conclusion: Whitepaper Marketing as Your Growth Catalyst
Recap & Next Steps
- Thought Leadership: Whitepapers help establish a business as an authority in cybersecurity.
- SEO & Lead Generation: When optimized properly, SEO-friendly copy can draw organic traffic and capture high-value leads for your marketing white paper.
- Brand Differentiation: Demonstrating mastery of complex security challenges sets smaller enterprises apart from competitors.
Final Thoughts
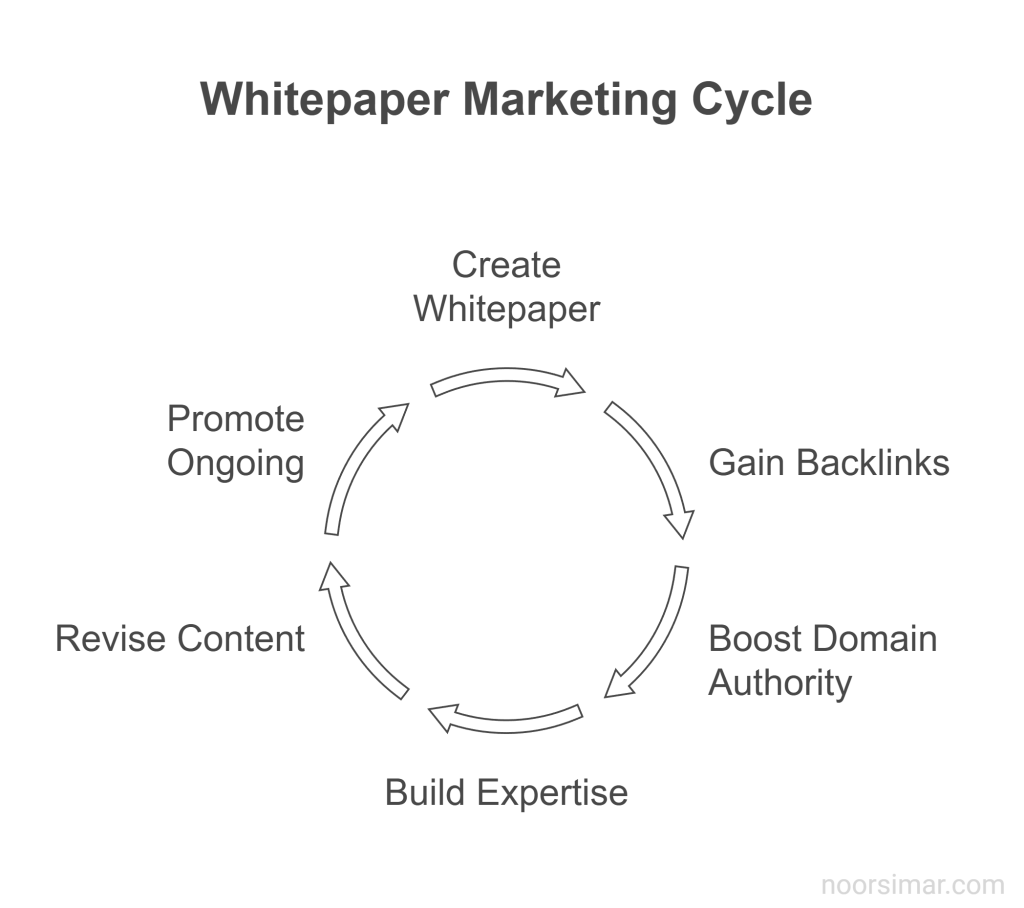
Whitepaper marketing offers a durable and scalable asset that tackles both brand awareness and lead generation. By harnessing the depth, credibility, and evergreen potential of a well-structured whitepaper, cybersecurity businesses can secure a formidable position in the digital market-gaining organic backlinks, boosted domain authority, and a reputation for unmatched expertise. Regular revisions and ongoing promotions will keep the content fresh, ensuring it remains a cornerstone of digital marketing success.
